API Keys
Overview
API Keys are generated and managed through the Noah Business Dashboard. They provide full access to our APIs for initiating financial operations, thus requiring stringent security measures. Remember:
- Never expose your API Keys in client-side code, public repositories like GitHub, or transfer them over unencrypted networks.
- Avoid internal broadcasting within your organization. Share API Keys only with authorized personnel.
- Secure Storage: The API Key is only visible at the time of creation and cannot be retrieved later. Ensure it is stored securely in your own systems.
- Regular Rotation: Rotate your API Keys periodically to minimize security risks.
Key Format
API Keys follow the format: <type>_<env>_<key>
type: Currentlyapikeyenv:sandbox|prodkey: A randomly generated string unique to your API Key
Example: apikey_prod_12345abcdef
Create API Keys
To access Noah's business APIs, you'll need to create an API key that serves as your unique authentication credential. This API key acts as a secure identifier that allows Noah's systems to verify your identity, track your usage, and ensure you have the appropriate permissions to access specific endpoints and data.
Start the API key generation process by logging into the Business Dashboard and clicking API in the Configuration section in the navigation bar on the left. In the API Keys section, click Create new.
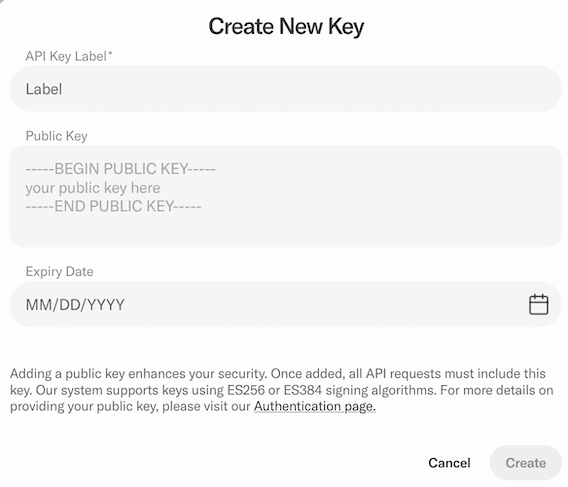
To facilitate easier testing with manual tools such as Postman, it is possible in our Sandbox environment to create an API Key without a Request Signing Public Key, allowing unsigned requests. However, before graduation to the Production environment, we require that at least one API Key is created with an associated Request Signing Public Key, so that we can verify your system is correctly signing requests.
Once generated, this key must be included in the header of each API request you make to Noah's services, enabling secure communication between your application and the Noah platform while maintaining proper access control and usage monitoring.
For further details, see Quick Start.